.CVE-2025-63421
Context
Comerc 32 is a commercial invoicing software developed by the Portuguese company Filosoft for Microsoft Windows.
Through a detailed analysis, I was able to identify a security vulnerability during the installation process which allows the user that is installing the program, to modify/replace a file placed in a temporary folder, which would then be moved by the install wizard into the installation folder as the uninstall binary.
The backdoor can then be triggered during the normal uninstall process through the control panel.
Technical Description
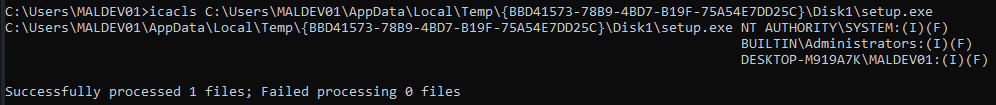
When installing the software through the installation binary comeinst.exe, the install wizard drops a file into a temporary folder in c:\Users\<user>\ApData\Local\temp, more specifically the file C:\Users\MALDEV01\AppData\Local\Temp\{random-UID}\Disk1\setup.exe. Since the user has write permissions (with low integrity token or without administrator shell) on this folder it's possible to overwrite the file original file with a backdoor:
Both setup.exe files are created by the installation process, first in the temporary data folders and then copied onto C:\Program Files (x86)\InstallShield Installation Information\{random-uid}\setup.exe:
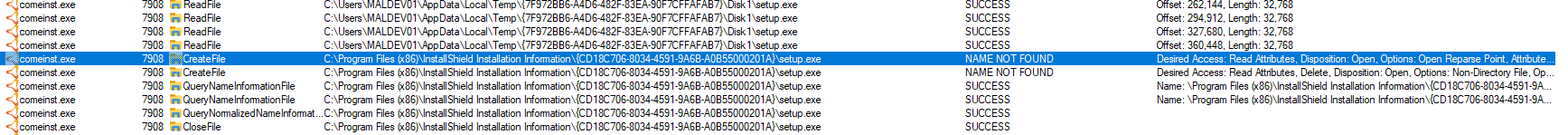
Exploitation is simple, the attacker just needs to replace the setup.exe on the temp folder with a backdoor before the installation process concludes, preserving the filename, on conclusion the comeinst.exe process doesn't validate the setup.exe file, copying it to C:\Program Files (x86)\InstallShield Installation Information\{random-uid}\. Once the same or another user tries to unninstall the program through the control panel, the confirmation prompt elevates the session token the user is using to high integrity, partially bypassing and obfuscating the backdoor execution since the UAC is triggered for the control panel process. Depending on the user that triggers the uninstall, the vulnerability further allows for a lateral movement attack vector.
The backdoor when executed without the exploit, has limited privileges as it is running with a lower integrity context:
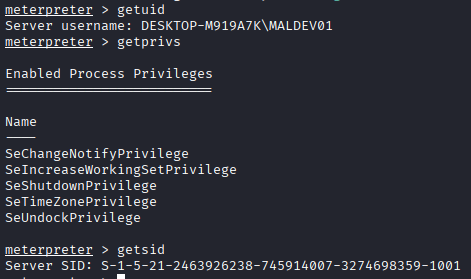
After performing the exploit full privileges are unlocked for the compromised user:

Impact
This vulnerability allows an attacker to either:
- Acquire all privileges associated with an initially compromised windows account without fully knowing it's credentials by partially bypassing the UAC security control.
- Allows the attacker to impersonate and escalate privileges as the user that initiated the uninstall process of the affected software, partially bypassing the UAC security control and further compromising the affected host or network.
It will have increased impact in environments with multiple administrator level users with different scopes, such as in a active directory domain. The attacker could trick a domain administrator into uninstalling an unauthorized software and hijack its account just by triggering the removal process through the control panel's "Programs and Features" menu.
The race condition against the install wizard and specific post-exploit trigger conditions will translate into a medium CVSS score.
CVE-ID: CVE-2025-63421
CVSS 4 Base Score: 5,4
CVSS 4 Vector: CVSS:4.0/AV:L/AC:L/AT:P/PR:L/UI:P/VC:H/VI:H/VA:H/SC:N/SI:N/SA:N
Afected Vendor: Filosoft.pt
Affected Product: Comerc.32 - Commercial Invoicing
Affected Version: 16.0.0.3
Mitigation
- Limit write permissions to the temporary setup.exe to NT Authority/System and Builtin/Administrators, even the user performing the installation should not be able to overwrite this file without an elevated context.
- Validate setup.exe file integrity before copying to its final location.
- Write setup.exe directly to its destined folder.
Timeline
10-2025 - Vulnerability Discovered
10-2025 - Vulnerability Submitted to Mitre
12-2025 - Filosoft contacted for reponsible disclosure coordenation - no answer
02-2026 - Full disclosure